Telegram OSINT VM Part 3
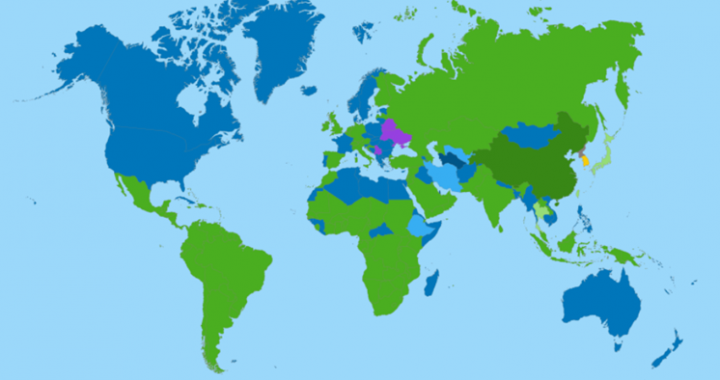
Thank you for returning to read the final part of the Telegram OSINT VM trilogy. This Blog is more my methodology of how I think when it comes to organising my work environment and some safeguards I take. I have my own methods that suit me as a person and how I work. As always take the bits that suit you and add your own flavours. I am a big believer of not just copying what some else has done but incorporating it into your own methodology and ideas. To give you some context to what follows. I use a Window host, this can be either Windows 10 or 11 depending on the device I have chosen. According to statista.com as of January 2023 Windows has just over a 74% share of the global OS market for desktop. Different websites will give you different figures but the one take away is that it is the most used OS globally. Again using statista.com Windows is the most targeted OS, 91% share of ransomware infections, ransomware is a form of malware, Fig 1.0 Fig 1.0 When we are using Telegram, depending on our deployment the above creates issues for Windows users. The following are the steps that I take to try and mitigate the risk. It is not 100% bulletproof. I would always encourage the use of malware / anti-virus protection software, for both your VM & host. I talked in the previous blogs how we can try and protect ourselves by disabling any form of auto-download on Telegram. If you ever download your full Telegram account, you maybe surprised to see what is in there. If you don’t take precautions there maybe malware in your account download. I know Linux and Mac users will be saying, well don’t use Windows, that unfortunately is not an option for the majority, either through restrictions at work, financial considerations or a lack of confidence to use Linux. This is also the case when considering using a device that can be reformatted. This would be a good option, that way if you do get infected you can reformat the device. You may consider just using a Windows VM for the same purposes, instead of relying on the Linux AV to scan for malware on your VM. Which ever route you take, ensure you have malware / antivirus software installed on both your host and VM. You must also remember neither Linux or MacOS are bulletproof and it would be a massive risk on the behalf of the user to think so. You have to make a decision as to whether you want to enable features that employ file sharing, like shared clipboard, as these are capable of spreading viruses between your virtual machine and host machine. It goes without saying that if you transfer files from your VM to your host then the malware will travel along for the ride. I set my Windows host up with an Admin & User account. I do not use the Admin account, I only use the User account. The reason being is that an admin account does not in the main require the password to execute programs whereas the User account ordinarily will. Some malware requires Admin privileges to run, so this is potentially our first line of defense. In File Explorer on Windows I would enable, ‘File Name Extensions’ so that you can see the full file name, this is to ensure there are no hidden .exe files. I also enable view hidden items. Fig 1.1 Windows 11: –
Fig 1.1 Fig 1.2 Windows 10: –
Fig 1.2 One good aspect of VMs is that you can create snapshots, a moment in time of how your VM was. I do not create snapshots of my Telegram OSINT VM. I create a master copy and then I will clone that creating a deployment VM. All my recording / auditing software for my deployment is on my host. At the end of each deployment session, anything I download / capture on my VM that I think is important I will transfer to my host.* *Whether you use snapshots or clone VMs, you need to be extremely careful of what you copy to your host make sure you have antivirus / malware protection on both your VM & host and ensure you scan before / after you transfer any files. If my deployment VM is compromised, I will spin up another VM from cloning my Master. The way I set out my VM files is illustrated below, Fig 1.3: – · Back Up VMs where I store my Master VMs. · Live VMs, VMs that I am currently using on a deployment. · Filed VMs, VMs that are no longer active on a deployment.
Fig 1.3 There are numerous ways of organising your work environment and software that you use. Hunchly is a good example of an auditing software however this may not be a option for everyone due to organisational or monetary constraints. I like to have a system where material is separated as sometimes I can’t see the wood for the trees. Below is how I set out my folders on both the host and VM. I create a desktop file, with various sub-folders. This is fluid and depends on my deployment specifics, Fig 1.4: –
Fig 1.4 At the end of that days deployment I will move what I need onto my host for safekeeping. I never delete anything from my VM as you never know if something you initially dismissed as not relevant becomes of interest but also if you work in Law Enforcement it maybe required for disclosure / discovery. I now have in place a system that I am confident that I can build a report from and that I am also able to bear witness to my work. The last consideration is how you safe-keep your work, do you leave it on your host, store in the Cloud or remove it from your host to an encrypted storage device offline. This will depend on your personal or organisational requirements. My preference is to store my work offline on an encrypted device. This may not be best for everyone, people who work from multiple locations, need to share their work with colleagues, Cloud storage maybe the best solution. Whichever solution you choose, like everything with OSINT make sure their is a methodology to your thinking. Don’t do something because that is the way it has always been done or because other people do it that way. What started out as one Blog ended up being a trilogy, I wanted to do justice to the subject matter. I hope that you have found my Telegram blogs useful, and thank you for staying with me. I always reach out to someone in the OSINT community to proof read my work, it is a great community and very supportive. I would like to take one last opportunity to say thank you to Griffin @hatless1der who was kind enough to proof read my work I give me some other ideas to consider.
Copyright 2023 © cqcore All Rights Reserved