I suppose there is a certain paradox in relation to having content about OSINT, OPSEC & Privacy on the same website. Why would someone who is involved in OSINT care about a person’s Privacy or why would someone who is keen on their Privacy care about OSINT or OPSEC.
I hope from the explanation below you will see how OSINT, OPSEC and Privacy are so closely linked and if we practice one discipline we should have a good working knowledge of the others.
An OSINT practitioner needs to understand the limitations of their work if they do not know how Privacy or OPSEC practices deployed by a subject may affect their ability to capture information or intelligence. Can they see this, understand it and can they circumnavigate it? They also need to understand the risk of being compromised by their own OPSEC practices. Do they understand that if they deploy tight Privacy practices on their accounts that this may effect what they can see of their subject.
A person who cherishes their Privacy needs to understand how it can be exploited by OSINT practitioners. What are the risks to people who do not practice Privacy or OPSEC.
OSINT
OSINT, stands for Open-Source Intelligence, which is a methodical driven approach to collecting, analysing and making decisions about data accessible in publicly available sources which is to form an intelligence picture of a subject, group, company, organisation or country.
It is probably true to say that OSINT has been around as long as it has been necessary to obtain information or intelligence. Certainly after both World Wars and the onset of the Cold War there was an uplift in the necessity to collect Open-Source Intelligence. As we have moved into the digital age, more information is publicly accessible and as our digital footprint expands so do the opportunities to obtain Open-Source Intelligence.
OPSEC
Operational security looks at what digital footprint risks we leave and how we can mitigate those risks. It encourages us to view our habits from the perspective of an adversary in order to protect sensitive information about ourselves or the fact that we are looking at them. What are our vulnerabilities and can they be discovered or exploited. It is not that we are trying to hide it is that we are trying not to be discovered.
Some measures we can take are free, some we will have to pay for, some measures are simple to implement some require more knowledge and application. The important point however is that we can increase our OPSEC and still enjoy our smart phones.
PRIVACY
The above two have their history firmly planted in the military and intelligence worlds, however with the advance of the digital age Privacy is also an important factor now.
I am not sure that while we use and carry around a smart phone, or other device that transmits and receives data that we can ever be 100% private. Can we really be expected to know what our smart phones and the apps on them are really doing. What we can do however is take steps either reasonable or extreme to reduce our digital footprint and increase our privacy.
What information we openly share or have to provide to be able to use a service can be potentially important personal identifiable information. We need to have some control over how our personal information is collected and used. The next data breach could expose you.
HOSTILE THREAT PROFILING
Putting all the above together, we can begin to see how individuals may be susceptible to hostile threat profiling. For people in positions of authority or influence this could be a vulnerability.
“Once effectively gathered, this intelligence can be used to locate an individual, identify patterns of life and target them accordingly. Many people are unaware of how they are sharing their personal details and what types of data may appear online. This is a particular risk for law enforcement, military, security services, diplomats and high profile people.”
David Benford, OSINT Trainer.
“A high-valued target can be anyone with privileged access and organizational influence, with access to sensitive information, or anyone with high levels of exposure and influence”
“Social exposure will inevitably lead to security & personal information leaks, especially when the high-valued target is not aware of essential security guidelines”
Christina Lekati, Social Engineer
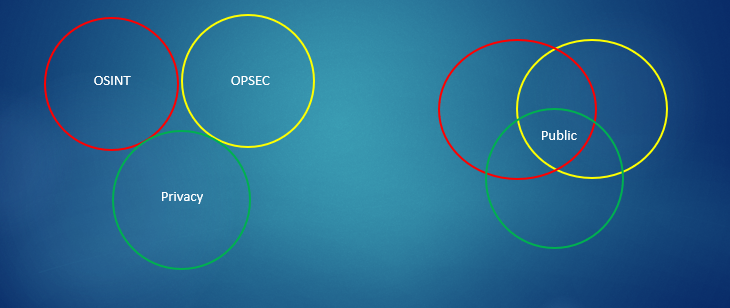
Ideally in the below image we would want the circles not to interlink however this is not realistic given the digital age we live in. We need to make the area where they do interlink as small as possible. We also need to understand that the circles may not interlink evenly and as a result we can assess where our vulnerabilities lie more accurately.
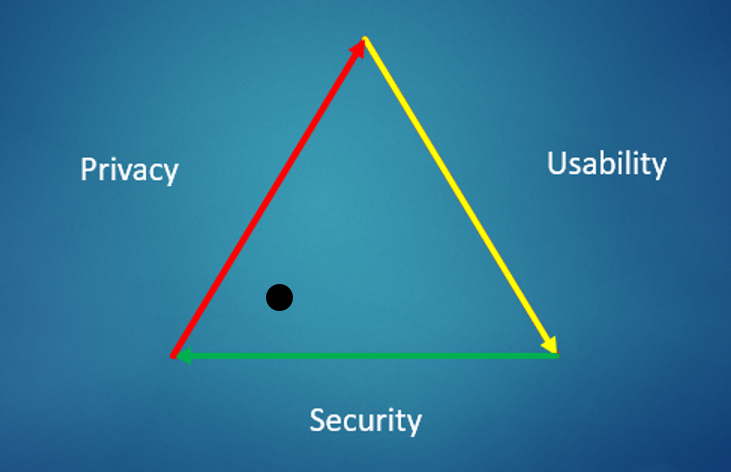
In the below image we can look at what we want from our digital devices in terms of Usability, Security & Privacy. I have chosen a more Secure and Private approach by placing a dot in the lower left corner, I have scarifised Usability. This may not be suitable for all, by moving the dot around the triangle you can see what is important to you and then you can be to work out how reasonable or extreme you strategy needs to be to achieve better Security and Privacy.
How you want to position the above circles or dot will depend on your own Threat Model which should be distinct to you.
Copyright © 2021 cqcore All Rights Reserved





